misc/HelloWorld (0 points)
Open the text file to find the text synt{j4yp0z3_g0_PGS}. Run the ROT13 cipher decoder on it to get the flag.
Answer: flag{w4lc0m3_t0_CTF}
misc/Survey (1 point)
Complete the end of CTF survey to get the flag.
Answer: flag{th4nk5_f0r_c0m1ng}
web/Let It Go (105 points)
I used the browser inspector to check the HTML for the page and found the flag in the DOM.
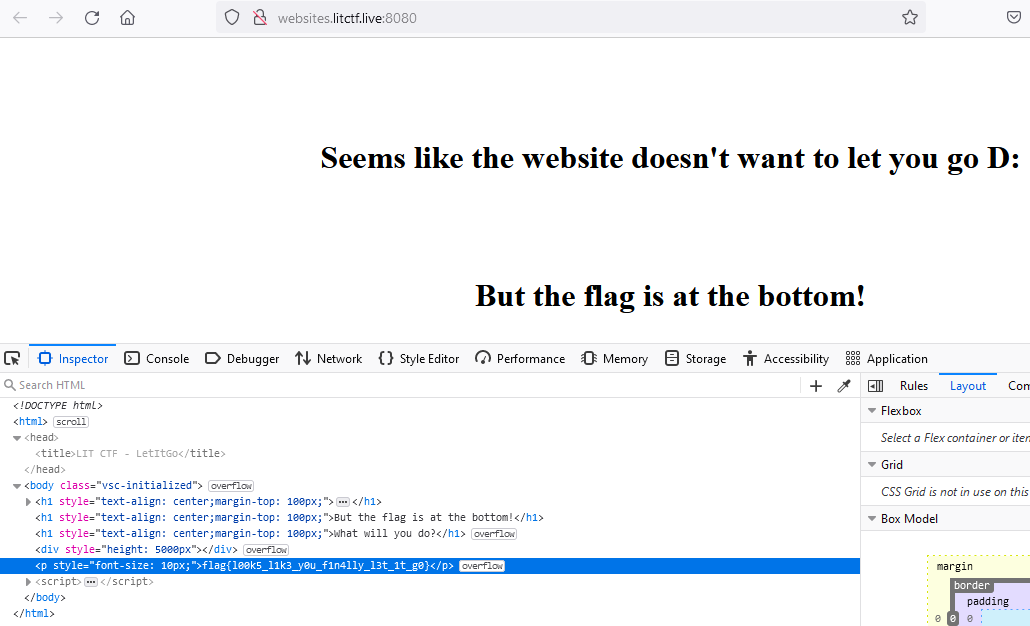
Answer: flag{l00k5_l1k3_y0u_f1n4lly_l3t_1t_g0}
crypto/7 More Caesar Salads (106 points)
Run the Caesar cipher decoder on the given cipher text mshn{Dlsjvtl_Av_Jyfwavnyhwof} with a letter shift of 20. This website can be helpful https://cryptii.com/ for encoding and decoding ciphers.
Answer: flag{Welcome_To_Cryptography}
misc/Hex to ASCII (106 points)
I used the command echo -n 666c61677b77346273317465355f346e645f7430306c355f3472335f793075725f673030645f667231336e64357d | xxd -r -p to convert the provided hex to ASCII. The flag was flag{w4bs1te5_4nd_t00l5_4r3_y0ur_g00d_fr13nd5}.
Answer: flag{w4bs1te5_4nd_t00l5_4r3_y0ur_g00d_fr13nd5}
misc/Intro To CTF (106 points)
Read the instructions and find the flag at the bottom of the page.
Answer: flag{h3ll0_w0r1d_y0ur_f1r5t_ctf}
misc/Peanutbutter.Jar (106 points)
Go to the provided website https://pbjar.github.io/ and find the flag commented out in the HTML.
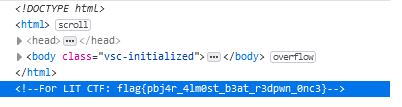
Answer: flag{pbj4r_4lm0st_b3at_r3dpwn_0nc3}
web/My First Website (107 points)
The flag is split into 3 parts on the webpage. The first part flag{1_l1k3_ is in a marquee tag near the bottom of the page. You can also search for the text flag to find it. The second part is commented out and be found in the DOM via searching for flag and finding the text 90s_w3bs1t3s_. The third part can be found from searching for } in the DOM. One of the hits, d351gns} looks like a likely candidate for the end of the flag. When fully assembled, the flag successfully validates.
Answer: flag{1_l1k3_90s_w3bs1t3s_d351gns}
misc/Discord Flag (107 points)
The flag can be found in the LIT Discord Announcements Channel.
Answer: flag{L1T_d1sc0rd_0rz}
web/dizzy (108 points)
The first time you arrive at the page, it redirects you to another page that does not have the flag before the 10 seconds are up. If you return to the previous page by “going back” a page, and wait 10 seconds, you will be redirected to a page with the flag.
Answer: flag{th1s_is_b4d_pr4ct1c3_app4ar3nt1y}
rev/Yarn (109 points)
I used the command xxd yarn | grep -i -A 4 flag ultimately get the flag. Using cat yarn | grep -i flag did not reveal the flag, so I tried parsing the ELF file with xxd to see if the flag would be visible via a hexdump instead of parsing the file directly as ASCII. It did show part of the flag, but the rest was not visible. I added -A 4 to pick up the lines that immediately followed the first line that cointained the flag. This was the output:
0000b780: 666c 6167 7b79 3472 6e5f 346e 645f 7331 flag{y4rn_4nd_s1
0000b790: 6c6b 5f34 7233 5f6e 3163 335f 6275 745f lk_4r3_n1c3_but_
0000b7a0: 7374 7231 6e67 735f 3173 5f77 6834 745f str1ngs_1s_wh4t_
0000b7b0: 6730 745f 7468 335f 666c 3467 7d00 0000 g0t_th3_fl4g}...
0000b7c0: 5965 6168 2c20 6469 6666 6572 656e 742e Yeah, different.
Afterwards I reassembled the flag and it was indeed correct.
Answer: flag{y4rn_4nd_s1lk_4r3_n1c3_but_str1ngs_1s_wh4t_g0t_th3_fl4g}
misc/Dots and Lines (109 points)
I used the website https://morsecode.world/international/decoder/audio-decoder-adaptive.html to decode the morse code audio file. Then I wrapped the output in the flag format, removed the preceding spaces in front of “M0RSE” and the flag successfully validated.
Answer: flag{M0RSE C0DE IS C00L}
crypto/Zzz (110 points)
I used https://www.boxentriq.com/code-breaking/cipher-identifier to determine what kind of cipher was used. The cipher used was a monoalphabetic cipher. The same site has a cipher solver, https://www.boxentriq.com/code-breaking/cryptogram , that correctly deciphered the provided text. Afterwards, we just have to format the output properly to get the flag.
Answer: flag{HOW_DO_YOU_KNOW_YOU_ARE_NOT_SLEEPING}
misc/Steganography (110 points)
I used StegSolve to find the flag by looking through the different color panes. The flag was visible in several of the planes including the one shown here, “Blue Pane 0”.
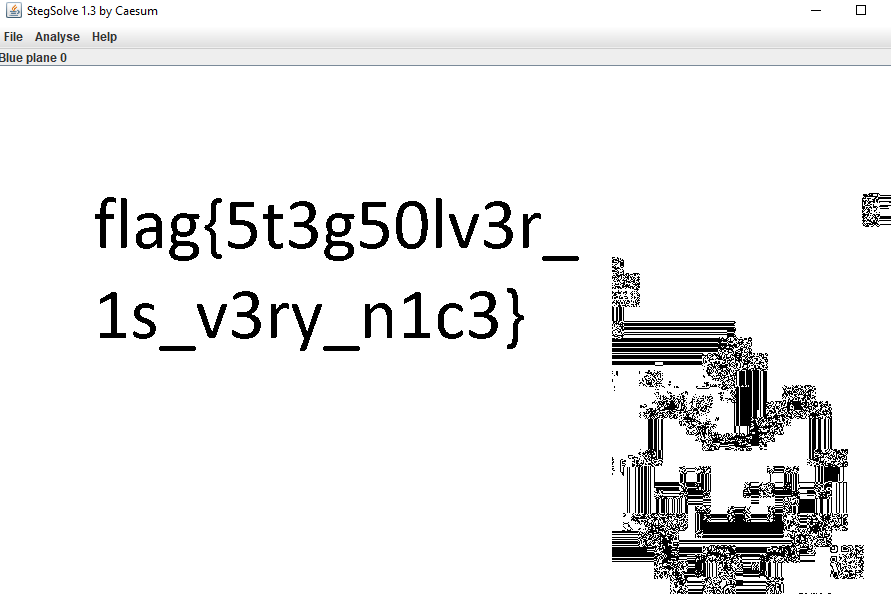
Answer: flag{5t3g50lv3r_1s_v3ry_n1c3}
rev/Evaluation (112 points)
Code after removing one set of “eval”’s:
You have to reverse the comparison string and then run the chr(ord(x)^5) on every character there.
['Correct flag!', 'Incorrect flag :(']
[''.join(
map(
lambda x: chr(ord(x)^5),
list(
input('Enter the flag: ').zfill(36)[::-1]
)
)
)!='x6wpf6vZ|w6sZq5kZv4Zk54q1fvpcg5~bdic']
Here is the python code I used for uncovering the flag:
org_str = "x6wpf6vZ|w6sZq5kZv4Zk54q1fvpcg5~bdic"
rev_str = org_str[::-1]
flag = []
for i in rev_str:
flag.append(chr(ord(i)^5))
flag = "".join(flag)
print(flag)
Answer: flag{0bfusc4t10n_1s_n0t_v3ry_s3cur3}
misc/Never Gonna Give You Up (113 points)
I saved the gif file and ran strings NeverGonnaGiveYouUp.gif | grep -i flag on it. It showed that “flag.txt” was somewhere in the file as a string. This means that there was likely a text file hidden inside of the gif file. I ran binwalk -e NeverGonnaGiveYouUp.gif to extract all hidden files that the program could see. In the directory that appeared, the flag.txt file had the correct flag.
Answer: flag{y0u_g0t_r1ck_r0lled_h4h4_g3t_r3kt}
misc/CodeTiger ORZ (114 points)
The audio is a false flag. There is nothing to decode there. The flag briefly flashes in the video at the 11 second mark. You can slow down the video speed to make it easier to spot.
Answer: flag{c0detiger_0rz}