Table of Contents:
Welcome (5 points)
Thanks for playing (5 points)
Feedback (5 points)
Basic (10 points)
Bad Developers (10 points)
Identifying an Attack (10 points)
Expic (15 points)
Wait, what! (20 points)
Where is this? (40 points)
WDigest (50 points)
Welcome (5 points)
The provided string is encoded in base64. You can use many different tools to decode it. I used the command echo -n UlRMe0g0VkVfRlVOX1BMNFkxTkchfQ== | base64 --decode to get the decoded flag.
Answer: RTL{H4VE_FUN_PL4Y1NG!}
Thanks for playing (5 points)
I searched Twitter using the organizers' discord nicknames. Searching “xentropy” led me to the correct organizer’s page where there was a post that contained a link to another page with the flag.
Answer: RTL{TH4NK2_F0R_PL4Y1NG}
Feedback (5 points)
Fill out the google form and the flag is given at the end.
Answer: RTL{TH4NK_Y0U_F0R_Y0UR_F33DB4CK}
Basic (10 points)
You can get the flag here with SQL Injection in either the username or the password field. In my case, I used the string ' OR 1=1-- to get the flag. “Flag: RTL{b@s1c_5ql}” showed up right below the Log In Button.
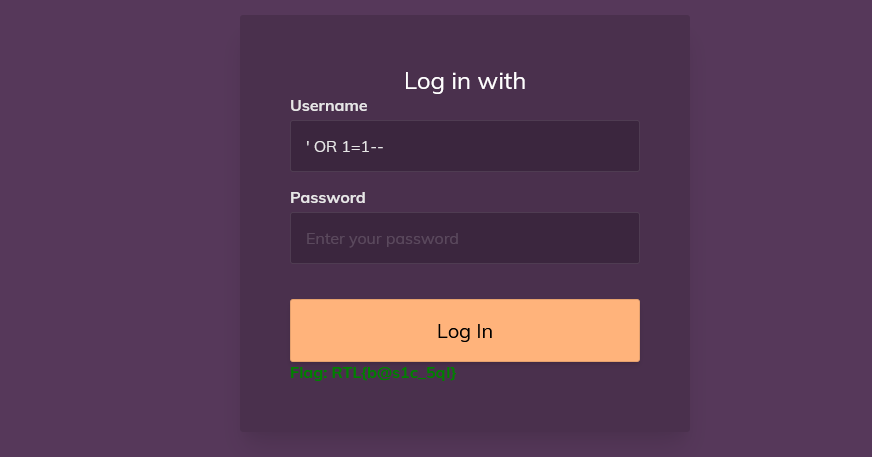
Answer: RTL{b@s1c_5ql}
Bad Developers (10 points)
I read the code and manually constructed the flag going in order from position 0 up to position 16 for the input that would work with the program.
Answer: RTL{D0NT_D0_TH1S}
Identifying an Attack (10 points)
I searched various terms using Google but eventually searching for “apple bluetooth rce cve” led me to a page from Apple that talked about fixing an remote code execution Bluetooth-based vulnerability on their devices. There are several CVEs on the page, but the first one that validated for me was CVE-2021-1794 after putting it into the proper flag format.
Answer: RTL{CVE-2021-1794}
Expic (15 points)
The program exiftool is useful here. While investigating the picture, I saw a “Number” field when I ran exiftool on it. This seemed like a strange name for a field so I though that it might be needed to get the flag.
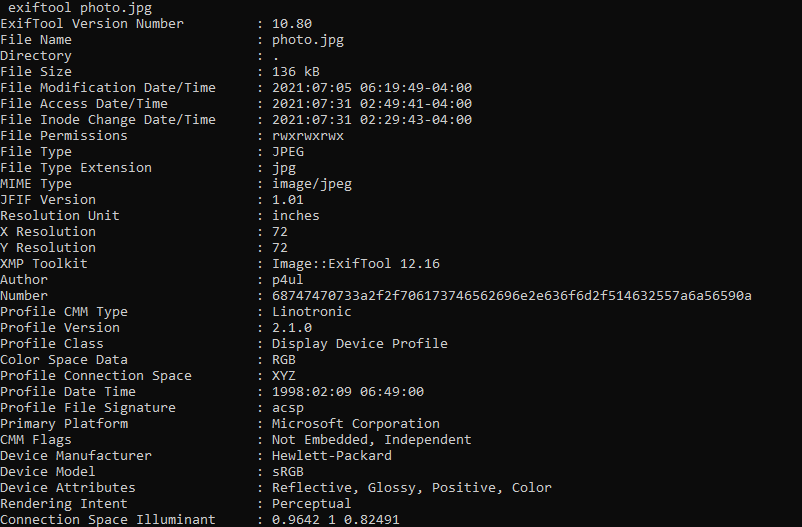
I converted the hex string there to ASCII which gave me a pastebin link that had a base64 string as paste data. After converting this string to ASCII from base64, the correct flag was there.
Answer: RTL{10bba9a52417095de51db9456361d744}
Wait, what! (20 points)
I used the hint to solve this problem. It mentions interwoven Caesar ciphers based on a key. After a bit of research, I found out that there is a cipher that fits the description, the “Vigenère cipher”. I used the Vigenère cipher from https://cryptii.com to solve the challenge. I noticed that while trying to guess the key, that entering 3 letter keys would greatly alter the first 3 letters in the flag. I eventually tried putting “RTL” as a key and saw “WIN” as the first 3 letters in the plain text. I then tried using “WIN” as the key and got back some plain text that turned out to be the correct flag.
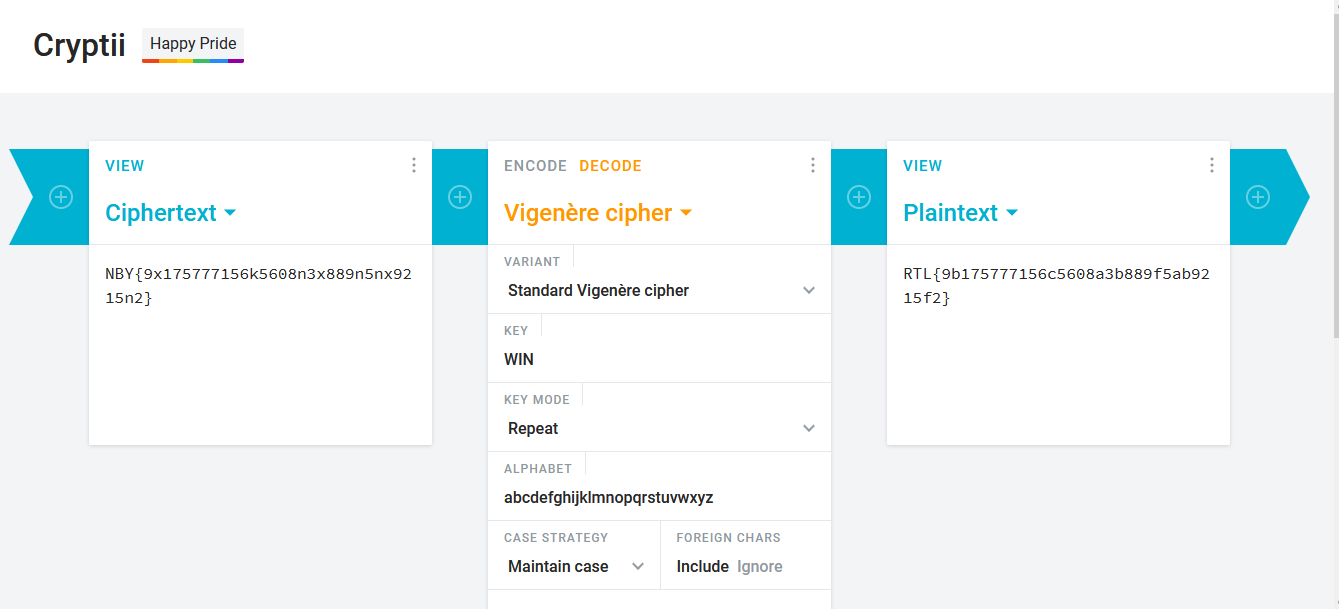
Answer: RTL{9b175777156c5608a3b889f5ab9215f2}
Where is this? (40 points)
I ran out of time on this challenge, but I was on the right track. First I tried to see if there was any clearly readable text in the picture, like from a store or building but I couldn’t find anything with the text that I could see. I next tried putting the image into Google Images and Yandex Images. Google Images didn’t lead anywhere but after cropping the picture in Yandex to only include the giant tower in the back and the building with a flag, I was able to find other pictures and eventually determine that the tower was “Fernsehturm Berlin” in Berlin, Germany. I then proceeded to Google Maps but I ran out of time before getting the exact position the picture was taken.
Answer: RTL{52.516_13.408}
WDigest (50 points)
We receive a lsass1.DMP file which contains the password somewhere inside. I used mimikatz to read the dump file by first starting up mimikatz, then in the mimikatz interface entering sekurlsa::minidump <path_to_dump_file> and sekurlsa::logonpasswords. The password which is the flag should be visible in the output.
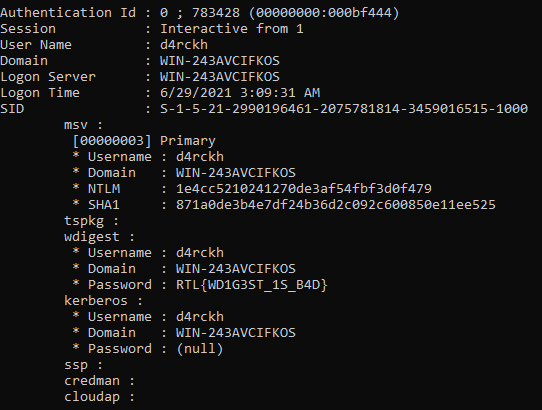
Answer: RTL{WD1G3ST_1S_B4D}