Secret Document (100 points)
I used the file command and discovered that the Classified.docx file was actually a pcap capture file. Opening it up in wireshark after changing the extension to .pcap revealed that a pdf file was being transferred via FTP when the packet capture was was running.
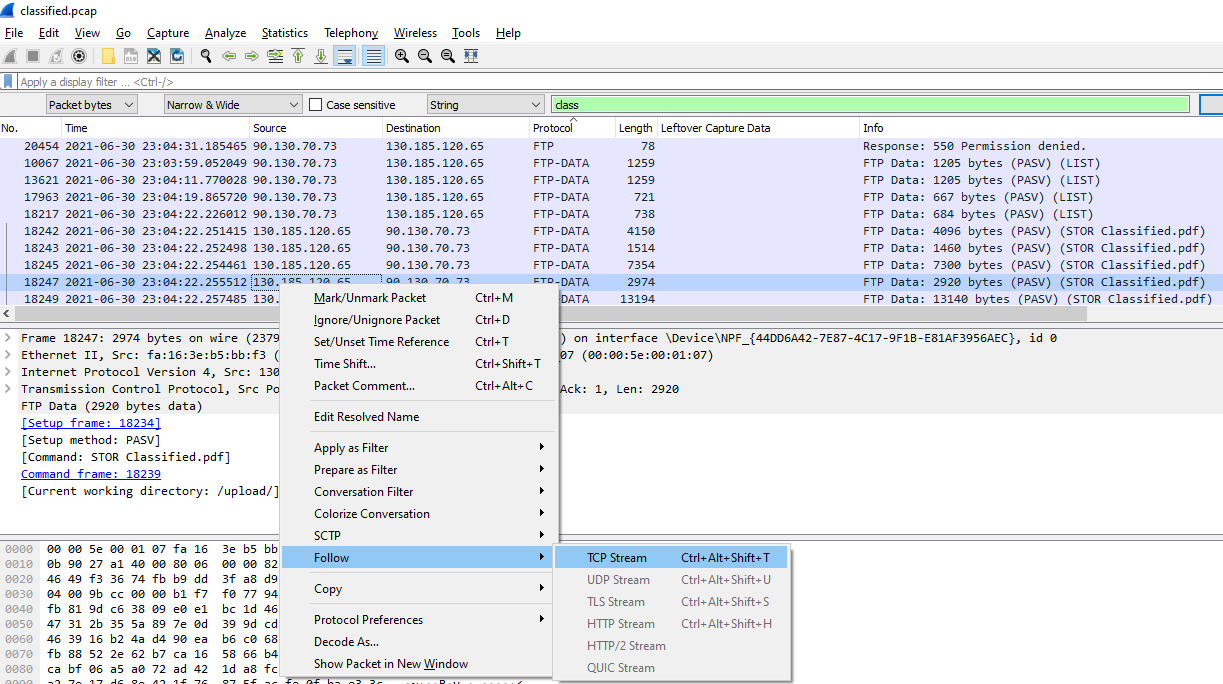
Following the TCP Stream for the Classified.pdf file and saving the data as “Raw” will give us the pdf file (you have to name the file and add the .pdf extension yourself). The flag is fully visible when the pdf file is opened up.
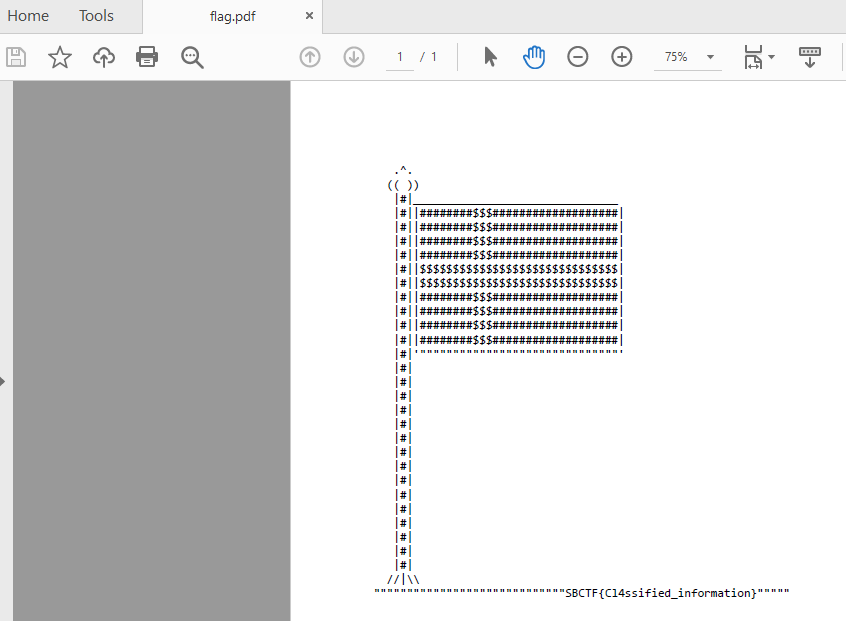
Answer: SBCTF{Cl4ssified_information}
Yummy Cookie (100 points)
The website gives hints about how to get the flag. The first hint is about orders, cookies, and cookie flavors.
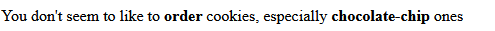
Adding a cookie to your browser with the name “order” and the value “chocolate-chip” and refreshing the page gets us to the next hint.
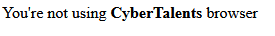
This is a hint to change our browser user agent to CyberTalents (This must be exact). After all of this, when you refresh the page, an alert shows up with the flag.
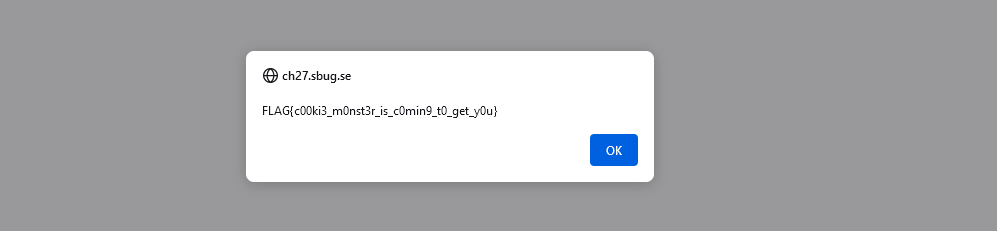
Answer: SBCTF{c00ki3_m0nst3r_is_c0min9_t0_get_y0u}
Simple Login (100 points)
Go to the login page and login with admin (Case insensitive) as the username. The password can be anything. Then go back to the home page. The flag will be displayed at the very bottom of the page.
Answer: SBCTF{g00d_0ld_l0g1n_pwwn}
War Enc (100 points)
We are given a .zip archive that once extracted shows the python file used to encrypt the flag, and the encrypted flag. The “MORSE_CODE_DICT” variable has the morse code mapping used to encrypt the flag. When I used the encoding to decode the flag, the first five letters were not “SBCTF”, so I knew that I needed to find what else was done to encrypt the flag. With a bit of trial and error, I found out that the letters were shifted 6 places with the Caesar Cipher and I just had to go in reverse to finally get the fully decrypted flag. This is the Python script that I used to solve the problem:
MORSE_CODE_DICT = { 'A':'.-', 'B':'-...',
'C':'-.-.', 'D':'-..', 'E':'.',
'F':'..-.', 'G':'--.', 'H':'....',
'I':'..', 'J':'.---', 'K':'-.-',
'L':'.-..', 'M':'--', 'N':'-.',
'O':'---', 'P':'.--.', 'Q':'--.-',
'R':'.-.', 'S':'...', 'T':'-',
'U':'..-', 'V':'...-', 'W':'.--',
'X':'-..-', 'Y':'-.--', 'Z':'--..',
'1':'.----', '2':'..---', '3':'...--',
'4':'....-', '5':'.....', '6':'-....',
'7':'--...', '8':'---..', '9':'----.',
'0':'-----', ', ':'--..--', '.':'.-.-.-',
'?':'..--..', '/':'-..-.', '}':'-....-',
'{':'-.--.', '_':'-.--.-'}
# Create Reversed Dictionary
REV_DICT = {value: key for key, value in MORSE_CODE_DICT.items()}
file = open("message", "r")
message = file.read()
message_list = message.split(" ")
flag_list = []
for i in message_list:
if i in REV_DICT:
flag_list.append(REV_DICT[i])
# Caesar Shift +6 letter positions
flag = []
for i in flag_list:
if i.isalpha():
if ((ord(i) + 6) > 90):
flag.append(chr(ord(i) - 20))
else:
flag.append(chr(ord(i) + 6))
else:
flag.append(i)
flag = "".join(flag)
# The flag inside the braces must be lowercase to successfully validate
flag = flag[:5] + flag[5:].lower()
print(flag)
Answer: SBCTF{send_reinforcements_we_are_under_heavy_fire}
Records (169 points)
The goal was to find the correct IP address in the first A record that the securebug.se domain used when they first switched to Cloudflare. I tried using dig and nslookup but only got the most up to date A records. Eventually while searching online, I found https://securitytrails.com which allows you to lookup historical DNS records for web domains for free. After making an account, I checked the historical records for securebug.se and one of the three IP addresses in the Cloudflare A record for July was the correct IP. The flag validated after putting the IP into the SBCTF{} format.
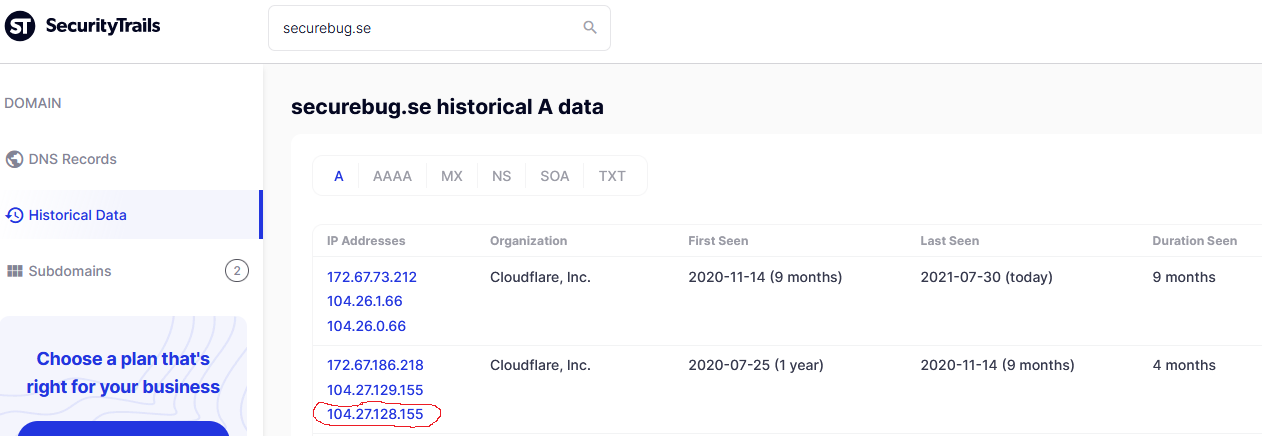
Answer: SBCTF{104.27.128.155}
Projan (233 points)
I opened the packet capture file in Wireshark and looked for anything of interest. Eventually I found something called “goog1e_born_help.exe” in one of the packets. I tried entering that with the flag format but it was not the answer. Eventually after a lot of trial and error when searching online, I realized that one of the tags associated with the .exe file on malware analysis websites was the correct name of the malware. I put the malware name, ponmocup in the flag format and it was marked correct.
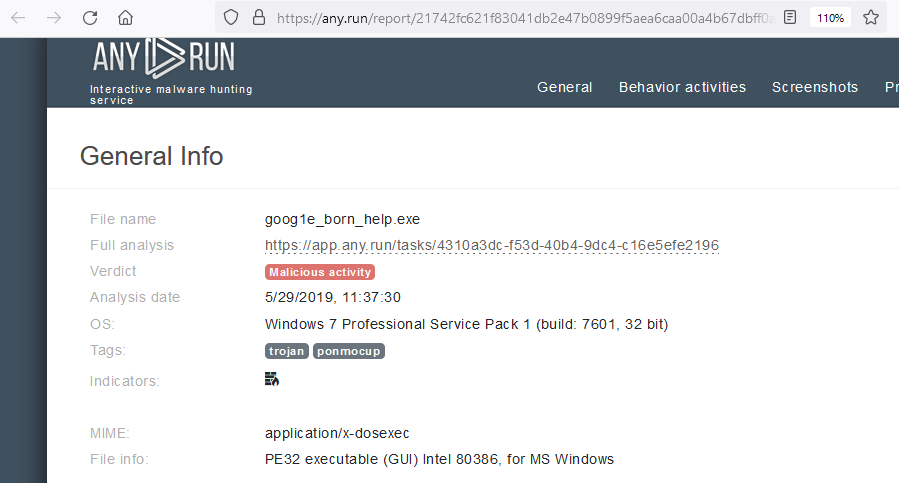
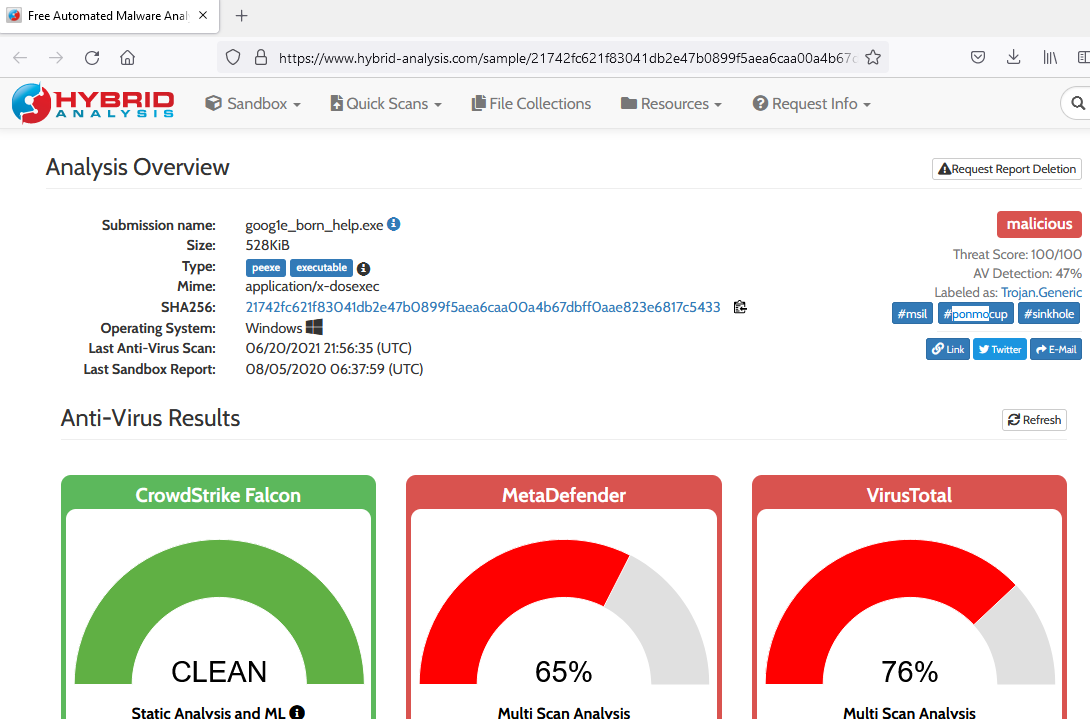
Answer: SBCTF{ponmocup}